Ethical review of COVID-19 research in the Netherlands; a mixed-method evaluation among medical research ethics committees and i

Frontiers | Individual-based and interactional resilience mechanisms in social and healthcare service NPOs during the COVID-19 pandemic: Handling a disruptive extreme context in Austria

A γ‐Strawman privacy‐preserving scheme in weighted social networks - Chen - 2016 - Security and Communication Networks - Wiley Online Library

PDF) Quasi-Identifier Recognition Algorithm for Privacy Preservation of Cloud Data Based on Risk Reidentification
The responsiveness of criminal networks to intentional attacks: Disrupting darknet drug trade | PLOS ONE

How Dare They Peep into My Private Life?”: Children's Rights Violations by Governments that Endorsed Online Learning During the Covid-19 Pandemic | HRW

PDF) A discrete choice experiment to examine the factors influencing consumers' willingness to purchase health apps
Algorithms | Free Full-Text | Feedback-Based Integration of the Whole Process of Data Anonymization in a Graphical Interface

PDF) Seeking help for peritoneal dialysis‐associated peritonitis: Patients' and families' intentions and actions. A mixed methods study

A γ‐Strawman privacy‐preserving scheme in weighted social networks - Chen - 2016 - Security and Communication Networks - Wiley Online Library
Virtual punishment in the making: When citizen journalism enables processes of shaming and online victimization Mallén, Agneta
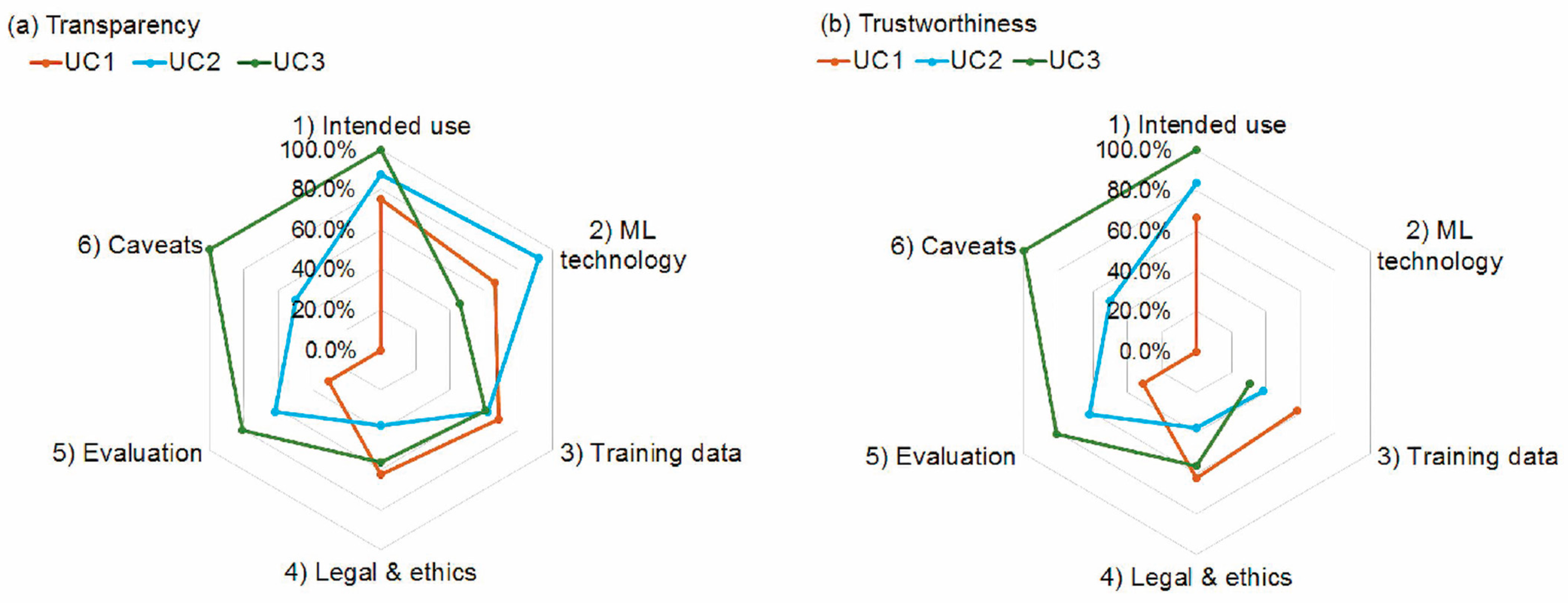
Healthcare | Free Full-Text | Piloting a Survey-Based Assessment of Transparency and Trustworthiness with Three Medical AI Tools