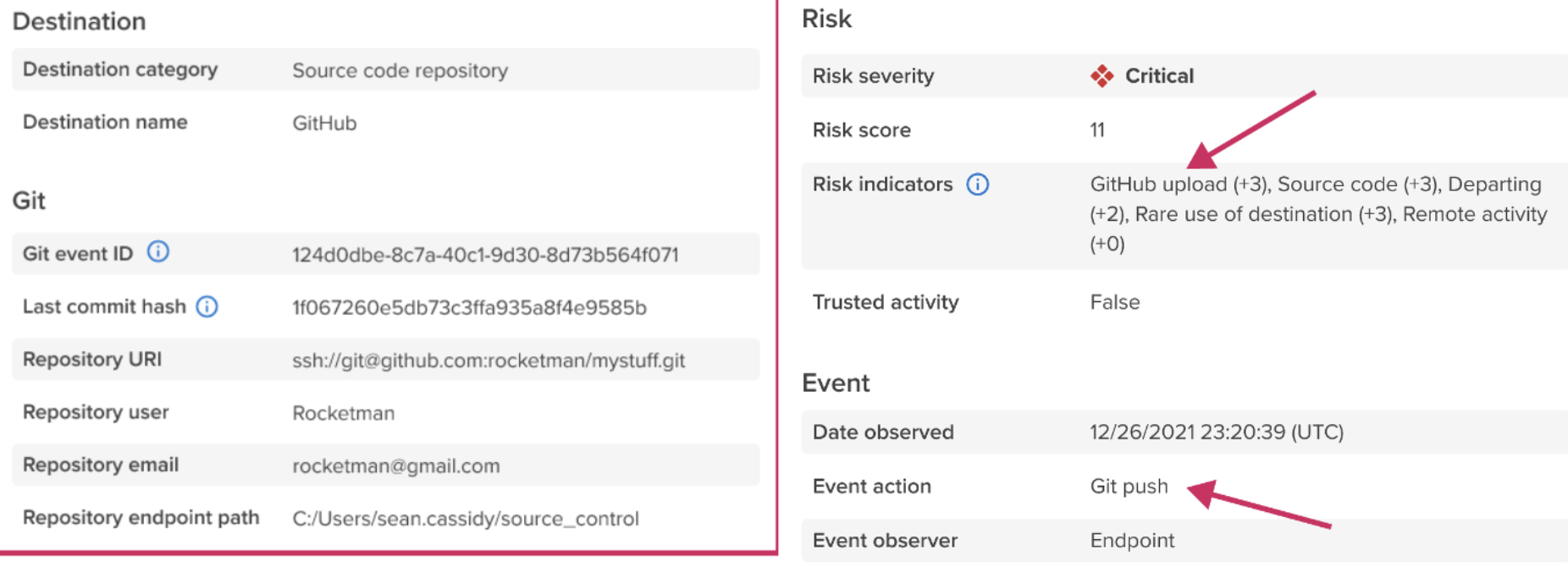
The Week that Was: Chinese threat actor hit US organizations with a Microsoft cloud exploit. Training code turns out to be malicious in a new proof-of-concept attack discovered on GitHub.
GitHub - benstew/awesome-data-exfiltration: Curated list of awesome, open source data exfiltration tools